How Does Digital Forensics Work?
Aidco Solutions team provides an extensive range of services that include Digital Forensics, Information Governance, Electronic Discovery, Data Analytics and Cyber Security. We provide a unique approach to complex business dispute and investigative matters, offering the latest technology to best serve our clients' needs. With experience in global markets and focused industry support, we help clients to manage vast amounts of electronic data, navigating legal and business processes whilst maximizing the value of information assets. With a principal laboratory and data center in Islamabad, our forensic technology specialists can offer the following services.
- Forensic acquisition (imaging of electronic devices, mobile devices, computers, laptops and servers)
- Acquisition of emails or folders from servers
- Data recovery and reconstruction (Deleted file analysis)
- Establishment of Investigative Support Systems
- Phishing Investigations
- Mobile device forensics
- E-discovery solutions, management and litigation support
- Cyber Forensic Readiness planning
- Malware and Key logger Analysis
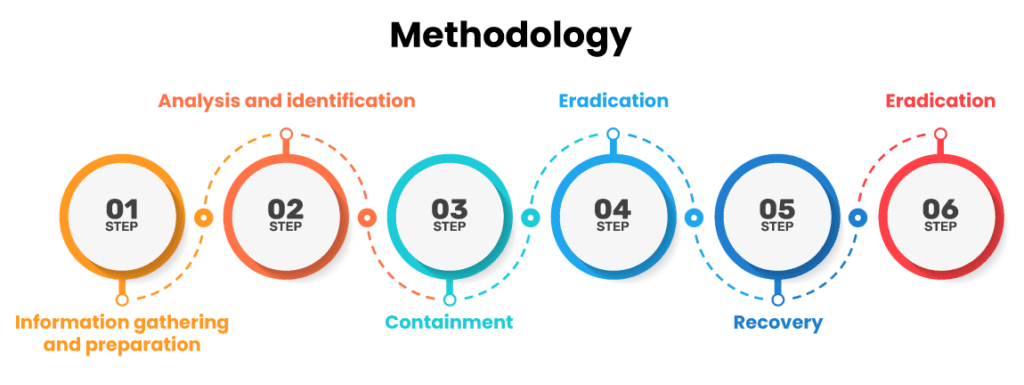
A step-by-step approach for Digital Forensics

Identify
Identifying an event from indicators and defining its type. It is significant as it affects other steps.

Prepare
Formulating tools, search warrants, management support, monitoring authorizations, and search warrants.

Preserve
Secure and preserve the state of physical and digital evidence so that it is admissible in the court of law

Collect
Collect the physical act and identical digital evidence using standardized and accepted procedures

Analyze
Determine significance, restructure fragments of data and draw inferences based on evidence originated. This might take several duplications and analysis to support a crime theory

Report
Summarize and offer a report of conclusions. Ensuring physical and digital assets are returned to the appropriate owner as well as defining how and what criminal evidence must be removed.
The benefits of digital forensic services

Support the data breach recovery process
Aidco digital forensic services form an integral part of an effective recovery plan, ensuring that you have the data, the facts, and the ability to build a strong narrative to support your case.

Limiting operational down time
Preparation is key to competent incident response, minimizing downtime, and helping you to restore your operations.

We are part of the world’s leading cybersecurity certification body, EC-Council.
We have highly qualified and experienced advisory and technical teams dedicated to helping organizations all around the world.
We are capable of providing you with a well-defined incident response plan through our experienced experts.
We are able to provide you with the relevant tools and knowledge to be efficient in incident response.

The approach that we have streamlined and adopted is flexible and can be tailored to your organization in order to help you to overcome your cybersecurity challenges.
We can help you mitigate damages to your organizations, improve communications between departments, and help prepare you to face future incidents with a lesson learned.
Identify
Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
-Cyber Security Posture Assessment
-Security Strategy and Transformation
-Vendor Risk Management
– IT Governance
– IT Risk Assessment
– ISO 27001 Advisory
– PCI-DSS Advisory
– Managed Security Services
– Identity and Access Management
– Training
– Data Privacy
Protect
Design and implement a control framework to protect the organization
Detect
Ongoing monitoring and checks to assess the preparedness of the organization to combat cyber security threats
– Vulnerability Assessment and Penetration Testing
– Secure Code Review
-Secure Software Development Lifecycle
– Cloud Security
-Software License Compliance
– Revenue Assurance
– Security Incident and Event Management (SIEM) & Security Operations (SOC)
Respond
Incident management in the event of a cyber security incident
Recover
Organizational resilience plans and restoration of services post a cyber security event
– Business Continuity Management / Disaster Recovery Planning
– Forensics Services
Enquire About Products and Solutions
Please complete the form below to tell us your business needs. A representative will contact you shortly
 Demos
Demos  Colors
Colors 
 Docs
Docs  Support
Support 

